
In this blog, we will review Symmetric and Asymmetric encryption methods.
Electronic communication is very vulnerable and because of this, your employees need to learn how to detect risks, use tools like encryption, and stay safe even from their home offices. Encryption is only one component of cryptography, in which an original plaintext or data is transformed into a ciphertext that prevents malicious third parties from understanding its content.
A cipher (or cypher) is an algorithm for performing encryption or decryption, transform a message into a random string Wikipedia says: “Cipher is originating from the Arabic word for zero صفر (sifr), the word “cipher” spread to Europe as part of the Arabic numeral system during the Middle Ages…. One theory for how the term came to refer to encoding is that the concept of zero was confusing to Europeans, and so the term came to refer to a message or communication that was not easily understood.”
There are two primary types of encryptions: Symmetric key encryption (or private key encryption) and Asymmetric key encryption (or public key encryption).
Symmetric Encryption
Symmetric encryption method uses single key to encrypt and decrypt the data.
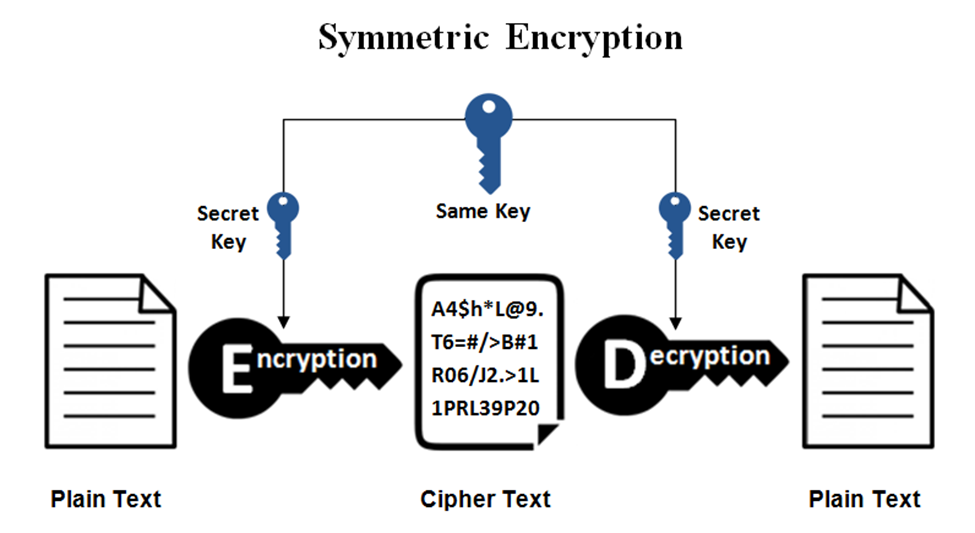
Symmetric encryption is fast, but less secure because of using one key it takes 128 or 256-bit key sizes. Symmetric Triple Data Encryption Standard (3-DES), Advanced Encryption Standard (AES) and Blowfish and Twofish are some symmetric encryption algorithms. In symmetric encryption, cipher-text attacks can be used to break the encryption.
Asymmetric Encryption
Asymmetric encryption uses two keys: a public key for encryption and a private key for decryption. It is not that easy to implement and manage due to its large key sizes.
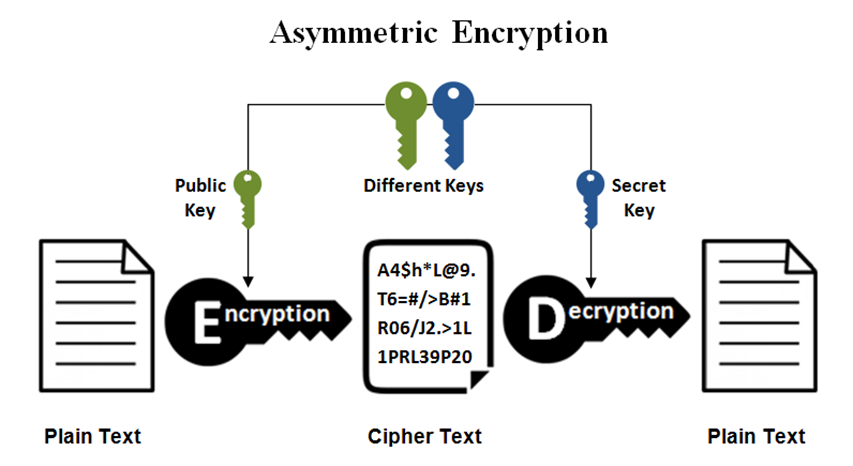
Asymmetric encryption uses Rivest Shamir Adleman (Ron Rivest, Adi Shamir, and Leonard Adleman: RSA), in 1024-bit to 2048-bit block sizes, Elliptic Curve Cryptography (ECC) or Digital Signature Algorithm (DSA) or more algorithms. Because of using two keys in encryption and decryption, asymmetric remains safer but slower, more complex and more resource intensive. RSA is considered one of the most secure and commonly used asymmetric key encryption algorithms. RSA is a great option if you only need to choose between security, time spent, or the amount of information encrypted. It is often used for encrypting lighter data such as digital signatures, SSL/TLS certificates, and browser applications. The biggest difference between ECC and RSA/DSA is the greater cryptographic strength that ECC offers for equivalent key size. An ECC key is more secure than an RSA or DSA key of the same size.
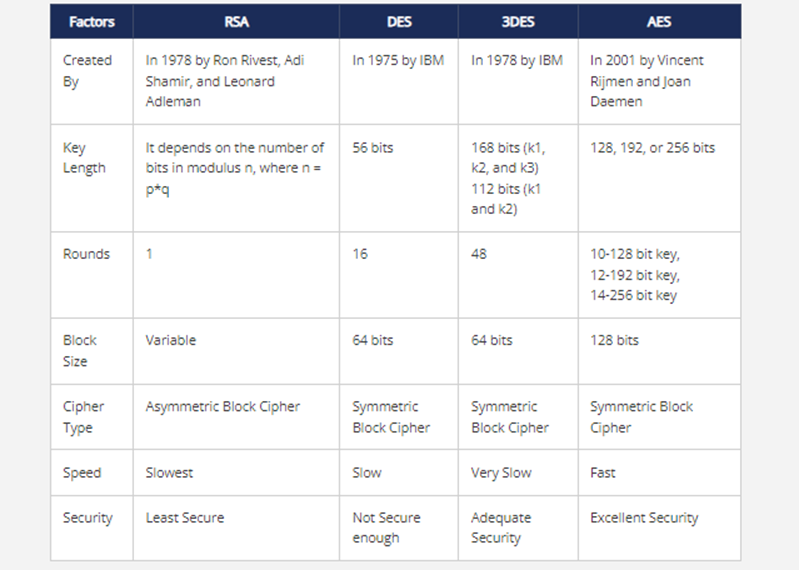
This table shows the main features of commonly used encryption algorithms:
Would you like to learn more about our services? Email [email protected] or call 289-803-9730. We would be happy to share more details about our self-service or fully managed eDiscovery services!





